The fundamentals of Exfiltration prevention start with Data Loss Prevention DLP. Below is a diagram of various DLP methods designed to prevent data from leaving an organization by various methods. Users often mistakenly send sensitive data in email text or attachments. DLP email scanning discovers and sequesters sensitive data before it is sent outside a safe boundary.
We created the diagram below to step through various scenarios explaining how various aspects of the system work step by step. Key to the conversation is what DLP protects and what it does not protect and why.
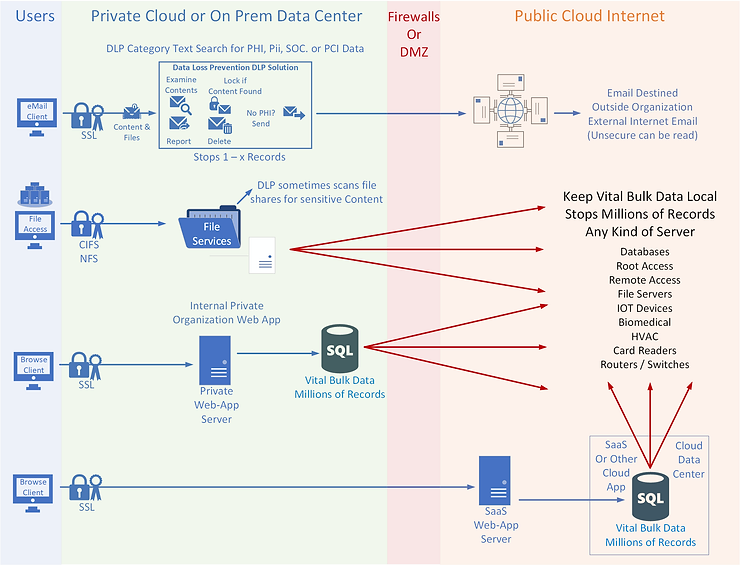
Encryption is key to data security, but there are ways attackers use encryption to evade detection. This is a significant issue for different DLP capabilities. Decryption is often employed in DLP scenarios, unless the encryption private certificate is not owned by the organization, as with most SaaS and external web applications.
These are essential concepts application developers, systems and network administrators need to understand to better protect an organization’s vital data.
Attend Exfiltration Prevention May 10-11 2022 Register for Austin Cyber Show Zoom Events
Join US and Canada cyber community members at the inaugural Austin Cyber Show Conference at Concordia University Texas, May 10-11. During the two-day cyber defense conference, participants can engage in discussions with peer leaders and industry experts on the cyber risks and challenges that businesses, leaders, developers, educators, and students face each day. Attendees will walk away with new insight and leadership lessons learned to defend against ransomware, phishing, and data exfiltration attacks. Five Cyber-By-Fire Skill Certificates are available to earn at the event and via Zoom Events online for 30 days afterward. Certain Zoom Event features only work in US/CAN.



